My today's blog is about the newly born malware. Before getting to that newly born malware let me firstly tell you what is the malware.
Malware is malicious software, is any software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It can appear in the form of executable code.
Ransomware is a type of malware which restricts access to the computer system that it infects, and demands a ransom paid to the creator of the malware in order for the restriction to be removed. Some forms of ransomware encrypt files on the system's hard drive while some may simply lock the system and display messages intended to coax the user into paying. Ransomware is a type of malware that tries to extort money from you. Crypto Locker, takes your files hostage and holds them for ransom, forcing you to pay hundreds of dollars to regain access. Most malware is no longer created by bored teenagers looking to cause some chaos. Much of the current malware is now produced by organized crime for profit and is becoming increasingly sophisticated.
Malware is malicious software, is any software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It can appear in the form of executable code.
Ransomware is a type of malware which restricts access to the computer system that it infects, and demands a ransom paid to the creator of the malware in order for the restriction to be removed. Some forms of ransomware encrypt files on the system's hard drive while some may simply lock the system and display messages intended to coax the user into paying. Ransomware is a type of malware that tries to extort money from you. Crypto Locker, takes your files hostage and holds them for ransom, forcing you to pay hundreds of dollars to regain access. Most malware is no longer created by bored teenagers looking to cause some chaos. Much of the current malware is now produced by organized crime for profit and is becoming increasingly sophisticated.
Fig 1: Ransomware
Ransomware typically propagates as a Trojan like a conventional computer worm, entering a system
through, for example, a downloaded file or vulnerability in a network service.
The program will then run a payload:
such as one that will begin to encrypt personal
files on the hard drive. More sophisticated ransomware may hybrid-encrypt the victim's plaintext with a random symmetric key and a fixed public key. The malware author is the
only party that knows the needed private decryption key. Some ransomware
payloads do not use encryption. In these cases, the payload is simply an
application designed to restrict interaction with the system, typically by
setting the Windows Shell to itself, or even modifying the master boot
record and/or partition table. Ransomware payloads utilize elements of scareware to extort money from the system's user.
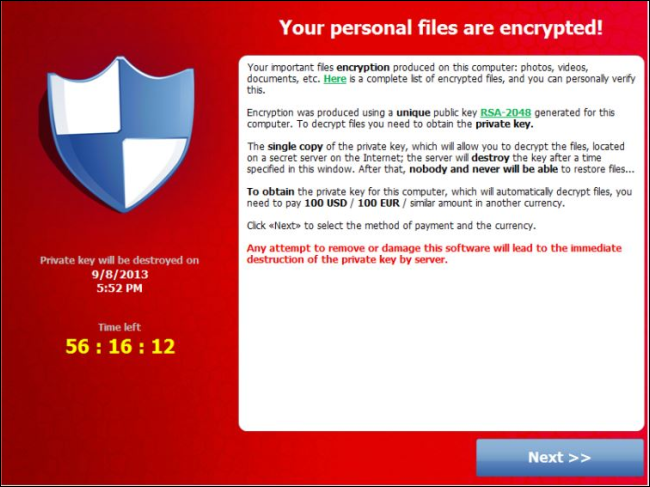
Fig 2: Ransomware affected system
How Ransomware Works:
Some ransomware may be disguised. It may function as
“scareware,” displaying a pop-up that says something like “Your computer is
infected, purchase this product to fix the infection” or “Your computer has
been used to download illegal files, pay a fine to continue using your
computer.”
Fig 3: Antivirus Encryption
Ransomware is becoming more and more sophisticated. One of
the latest examples, Crypto Locker, starts encrypting your personal files as soon as it
gains access to your system, preventing access to the files without knowing the
encryption key.
Protecting Your Files from Ransomware:
1) When backing up files, be sure to back up your personal files to a location where they can’t be
written to or erased.
2) Don’t just store your backups on an internal hard drive or
network share you have write access to.
3) Frequent backups are also important.
4) If your files do become locked by ransomware and you don’t
have the appropriate backups, you can try recovering
them with Shadow Explorer.
5) Crypto Locker has been verified to arrive through email
attachments, via the Java plug-in, and installed on computers that are part of
the Zeus botnet.
6) Use a good antivirus product that will attempt to stop
ransomware in its tracks.
7) Avoid running suspicious files. Ransomware can arrive in
.exe files attached to emails, from illicit websites containing pirated
software, or anywhere else that malware comes from. Be alert and exercise
caution over the files you download and run.
8) Keep your software updated.
Hence friends be aware while doing your any transactions and safeguard your mails Ids and password with proper measures.


No comments:
Post a Comment