Hey friends,
today we all will deal with the one of the new concepts called as Fine Grained Password
Policy, abbreviated as “FGPP”.
This concept
is mostly used in server 2k8. We cannot assign multiple password policies on
different OU within a domain. The default password policy will always override
any other password policy one may try to create in different GPO and different
level of linking, no matter what one can do, force the policy, block
inheritance, even remove the password configuration in the default domain
policy or set it to not configured.
Function of Fine Grained Policy Feature:
You can use fine-grained password policies to specify multiple password policies in a single domain and apply different restrictions for password and account lockout policies to different sets of users in a domain.Ways to configure Fine Grained policy:
For
implementing fine-grained password policies we need to perform the following
steps but first we need to define the following requirements.
Parameters
|
Designations
|
Enforce
password history
|
number of passwords to remember
|
Maximum
password age
|
number of days before a password
expires
|
Minimum
password age
|
minimum number of days a password
should not be changeable
|
Minimum
password length
|
length of password
|
Passwords
must meet complexity requirements
|
Enable/Disable whether password
should be complex or not
|
Account
lockout duration
|
Amount of time in minutes
|
Account
lockout threshold
|
Amount of time in minutes
|
Reset
account lockout counter after
|
Amount of time in minutes
|
Follow the below mentioned steps for applying the fine
grained policy
Log on to domain controllers, open ADSI Edit snap-in
- In Start -> select Run option -> type MMC.
- Then in File menu, select Add/Remove Snap-in.
- Select ADSI Edit, -> click on Add -> click OK.

Fig 1. Add or Remove Snap-in
2. In the ADSI Edit snap-in, right-click ADSI Edit -> click
Connect to.
3. In the Name field, enter the domain name -> click OK.

Fig2. Console Window
4. Expand the tree.

Fig3. Expanded Tree Structure
5. Right-click on the container -> New -> Object.
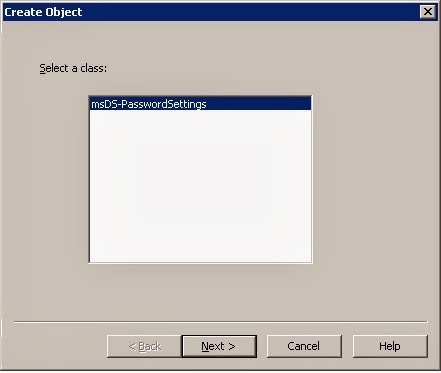
Fig4. Creating New Object
6. In the Create Object dialog box click msDC-PasswordSettings -> click next.

Fig5.
Object Dialog Box
7. Click Next -> Finish.
8. Right-click on freshly created object in the console tree
-> select Properties.

Fig6. Object Properties Window
9. Press edit.

Fig7. Object Properties Window
10. Click “Add Windows
Account.”
11. Press OK ->
Apply
12. You did it..!
Next time a user needs to change
password, the above PSO will be in effect. You need to deploy immediately the
PSO, just go to Active Directory Users and Computers and select “User must
change password at next logon” under User properties. If you try to logging on
with an account that has expired password or a newly created account, you will
be prompted to change the password.
No comments:
Post a Comment